Highlights from the research
- The healthcare sector was the most-targeted industry for ransomware during the third quarter of 2022, with one in 42 organisations impacted by ransomware.
- 78% of CISOs have 16 or more tools in their cyber security vendor portfolio and they concluded that having too many security vendors results in complex security operations and increased security headcount
What is the most-effective way to achieve cyber resilience?
Do you consolidate your security, or adopt a best-of-breed vendor approach?
It’s a long-debated topic within IT circles, with each option offering viable technical and business arguments.
And, as a CISO, every conclusion you come to will impact your cyber security effectiveness for years to come.
A recent survey by the Ponemon Institute stated that more than 20% of healthcare organisations reported increased patient mortality rates after experiencing a significant cyber attack; and another 57% said they experience poor patient outcomes.
Additionally, the study identified four common types of attacks: cloud compromise, ransomware, business email compromise/phishing, and supply chain.
Disruptive and deadly
Successful cyber attacks on healthcare organisations can be disruptive and even deadly.
Check Point Research (CPR) reported that, on average, the healthcare sector experienced 1,426 weekly attacks, a 60% increase in 2022 over the previous year.
And some of the most-high-profile attacks have targeted healthcare organisations.
In recent weeks, it was reported that the NHS had suffered a ransomware attack and several services, including NHS 111, some urgent treatment centres, and some mental health providers were taken offline.
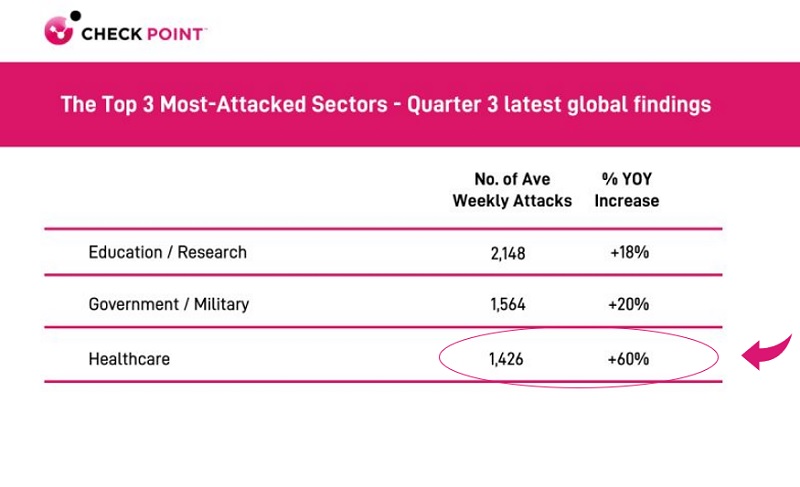
The Top 3 targeted industries. Attacks on healthcare grew 60% year on year
Deryck Mitchelson, field CISO at Check Point, said the NHS’s threat landscape has grown significantly, with the increased likelihood of major cyber attacks at any time.
Today’s ransomware economy is a complex operation, extorting millions of dollars per ransom and holding entire organisations captive under the threat of a total system shutdown.
As a business model, Ransomware-as-a-Service (RaaS) has seen the appearance of low-cost affiliate programmes for any criminal to get involved.
In one recent case, ‘diabolical’ is the term used to describe a cyber attack on a major Paris hospital where a wide range of IT systems were paralysed, and the threat actor demanded $10m to unlock them and threatened to release patient data.
In the attack’s aftermath, hospital staff struggled to provide emergency services and patient data and prescriptions had to be handled manually.
Sensitive information
When exploring why this particular industry seems to be so heavily attacked, one of the key reasons could be around the massive amount of sensitive and confidential patient information collected, which could be worth millions to attackers via blackmail or specific attacks on individuals.
Today’s ransomware economy is a complex operation, extorting millions of dollars per ransom and holding entire organisations captive under the threat of a total system shutdown
A case in point was the recent Medibank breach, Australia's largest health insurer, where hackers who stole customer data also released a file of pregnancy terminations.
With the increasing digitalisation across every industry, the healthcare industry is also facing an explosion of IoT and medical devices like insulin pumps and defibrillators, opening up more entry points for attacks, especially as security was not a primary concern in the design of such devices, many of which are sitting on flat networks and are not managed by the digital and security teams.
Attackers are also aware that such a critical industry like hospitals and medical centres cannot allow downtime or have medical systems which cannot work, as this will impact not just its reputation, but also place lives at stake.
Coupled by limited funds to spend on cyber security – with a higher preference to spend instead on medical supplies and improvement of medical systems – and a lack of cyber education among the healthcare workers, means the healthcare industry will continue to see cyber attacks for some time to come.
A complex attack surface
Besides ransomware attacks, healthcare organisations – in line with every industry – can expect to experience a vast array of attack methods, including phishing, various botnet attacks, distributed denial of service, and more.
And the challenges of the healthcare system’s multi-vendor environment – including hospitals, clinics, labs, and other medical environments – offers a broad and complex attack surface.
These facilities include networks, cloud infrastructure, desktop, and mobile endpoints, as well as network connected IoT devices.
The latter are sensor-driven medical devices that track and monitor in real-time, and most are not designed with security in mind.
Healthcare providers’ dynamic environments also introduce complex layers of user types and access privilege levels that can make sensitive personally identifiable information (PII) and other medical data ripe for cyber thieves.
Attackers are aware that such a critical industry like hospitals and medical centres cannot allow downtime or have medical systems which cannot work, as this will impact not just its reputation, but also place lives at stake
The cost of a breach in the healthcare industry went up 42% in the past 24 months.
For the 12th year in a row, healthcare had the highest average data breach cost of any industry with an average total cost of a breach ballooning at $10.10m (Source: IBM and CPR).
Given the facts, is security consolidation a viable option for healthcare professionals?
And, if so, how will it enhance an organisation’s security posture, improve security operational efficiency, and reduce total cost of ownership?
In its CISO Effectiveness Survey, Gartner reported that 78% of CISOs have 16 or more tools in their cyber security vendor portfolio; and 12% have 46 or more.
Building integration
It concluded that having too many security vendors results in complex security operations and increased security headcount.
Eight per cent of respondents saw vendor consolidation as an avenue for a more-efficient security strategy.
But, when IT budgets are often constrained, the question arises: How do healthcare CISOs deal with the bloat of security products?
Consolidation is a big desire from customers – possibly a response to the tool sprawl we mentioned earlier.
There is a feeling in the market that there might already be too many companies, so it’s not just about more innovation, but also building integrated platforms so customers can go to one place and get more baskets of services.
Moving forward
Healthcare depends on innovative solutions and services, and any disruption can endanger lives and livelihoods.
So, what actions can CISOs take to better ensure the protection of their organisations?
One answer is to consider the use of a consolidated security platform designed to guard against today’s critical zero-day and fifth-generation threats across the network, cloud, IoT, and endpoints.
There is a feeling in the market that there might already be too many companies, so it’s not just about more innovation, but also building integrated platforms so customers can go to one place and get more baskets of services
Consolidation is also a key benefit to cutting complexity to reduce cyber risks, a prediction Check Point Research also foresaw as part of its 2023 predictions.
With the cyber skills gap growing by over 25% in 2022, and organisations having more-complex, distributed networks and cloud deployments as an outcome of the pandemic, security leaders need a consolidation strategy to simplify their security operations, provide full end-to-end visibility, and improve their defences.
Without this, threat actors will continue to exploit weaknesses and vulnerabilities.
